Core Vulnerability Mechanism
The attack exploited a design flaw where short position operations immediately updatedglobalShortAveragePrices, which directly impacted AUM calculations used for GLP token minting and redemption. The attacker used reentrancy to establish massive short positions within a single transaction, artificially inflating GLP prices.
The critical vulnerability chain:
- Reentrancy entry point:
executeDecreaseOrderaccepted a contract address instead of EOA - State manipulation: Opening short positions immediately updated global averages
- AUM inflation: System counted unrealized short losses as vault “assets”
- Value extraction: Inflated AUM allowed redemption of GLP for excessive assets
How AUM Calculation Was Exploited
Normal AUM Calculation
GMX calculates its total value using this formula:- Average price at which all shorts were opened
- Current market price of the asset
- Difference = profit/loss for the protocol
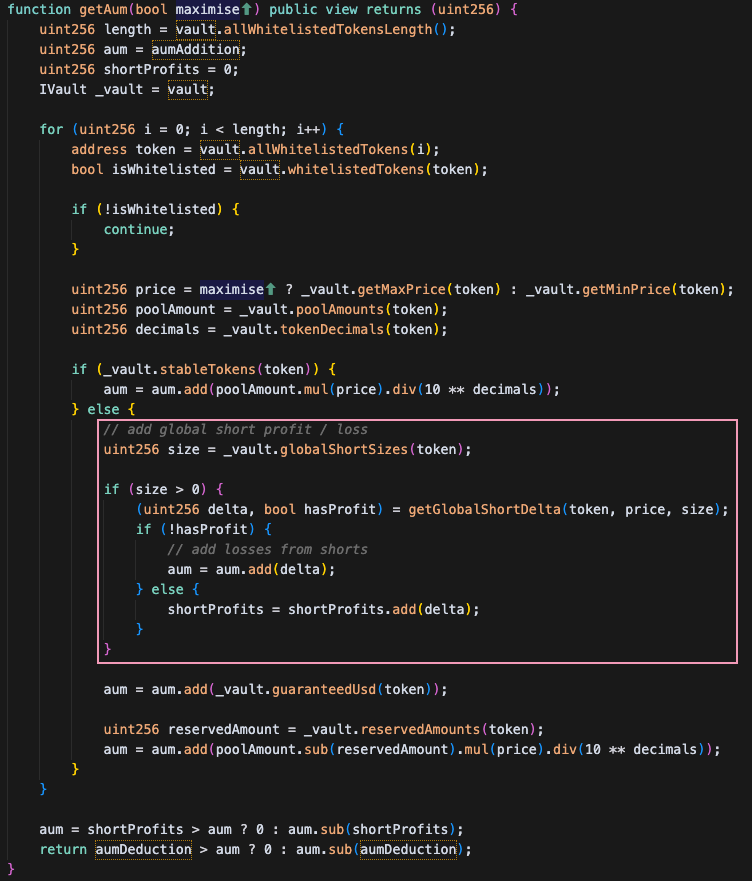
Key Insight: Short Position Impact
The critical part is how short positions affect AUM:- When shorts lose money (current price > average price): Vault profits, AUM increases
- When shorts make money (current price < average price): Vault loses, AUM decreases
The Manipulation
- Attacker deposited tokens to mint GLP (liquidity provider tokens)
- Exploited reentrancy to gain control during a transaction
- Opened massive short positions at artificially low average prices
- AUM spiked significantly because the system thought it had huge unrealized profits from shorts
- Redeemed GLP tokens at the inflated price, withdrawing $40M+ in real assets
Critical Invariants That Could Have Prevented the Attack
Multiple invariants could have detected this attack, but AUM manipulation bounds is probably the most obvious and versatile detection method, because it defines a behavior that should never happen. Here are some invariants that could have prevented the attack:1. AUM Manipulation Bounds Invariant
Implement a simple check that AUM changes must be reasonable. This invariant ensures that any change in the protocol’s total value is bounded by actual token flows and reasonable market movements.2. Atomic State Consistency Invariant
Ensure all state changes affecting token pricing complete atomically before any external calls. This prevents reentrancy-based manipulation of global price averages.3. Price Update Monotonicity Invariant
Ensure global average prices update based on actual position changes, not synthetic operations. This maintains mathematical consistency in price calculations.4. Caller Type Restriction Invariant
Critical financial operations must originate from externally owned accounts (EOAs) or pre-approved contracts. This prevents malicious contracts from exploiting reentrancy vulnerabilities.5. Position-to-Pool Ratio Invariant
Individual positions must not exceed a maximum percentage of total pool value. This limits the impact any single position can have on global averages.AUM Manipulation Bounds Assertion Example
A Credible Layer assertion similar to the one below could have prevented an attack like this. We have simplified the assertion for brevity, but a real world assertion would check for each call in the call stack that the invariant holds. In the example we just show the logic that would be checked for one call. Being able to inspect the call stack is a powerful feature of the Credible Layer and it allows for detection of attacks that are carried out in a single transaction.How This Assertion Catches the Exploit
This assertion implements a simple but powerful economic sanity check that would have prevented the GMX attack: What it does:- Captures AUM before and after the transaction using Phylax’s state forking
- Calculates the percentage change in AUM during the transaction
- Enforces a 5% maximum deviation - any AUM change larger than 5% triggers a revert (example value, could be higher or lower depending on the protocol)
- Adds an absolute cap of $10M for any single AUM increase (example value, could be higher or lower depending on the protocol)
- Percentage check: The artificial AUM increase represented a huge percentage change, far exceeding the 5% limit
- Absolute check: The artificial increase also exceeded the $10M absolute cap
- Economic logic: Real market movements rarely cause such extreme AUM swings in a single transaction

