Introduction
Phylax’s real-time security system detects and pre-emptively removes exploits before losses can be realized.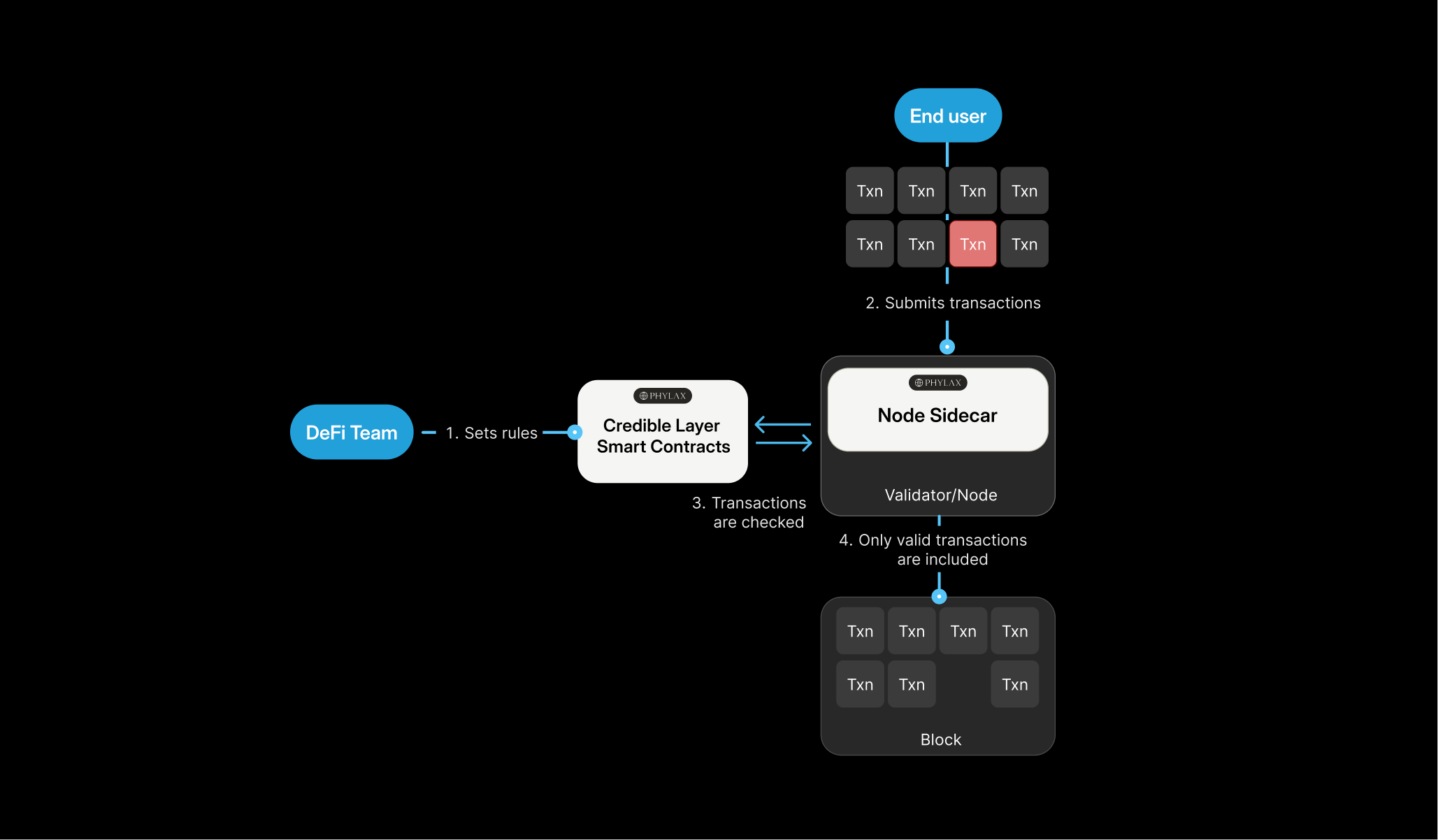
The Credible Layer is a network extension that lets protocols define security rules and enforces them at the network level. Transactions that would violate these rules are dropped before they can execute, preventing exploits rather than detecting them after the damage is done.
- Security rules are defined by the protocol team and deployed on-chain as assertions
- The network validates every transaction against relevant assertions before adding them to blocks
- Invalid transactions are dropped. If an assertion fails, the transaction never executes
Easy to adopt
- Written in Solidity with familiar Forge patterns
- No contract modifications or downtime required
- Works with immutable contracts
- All rules are publicly verifiable on the transparency dashboard
- Implementation effort is comparable to writing Forge invariant tests
Use Cases
Assertions enable a wide range of security and compliance use cases:Parameter Protection
Prevent unauthorized changes to critical protocol parameters such as owner and implementation addresses
Market Integrity
Ensure market prices don’t move beyond specified thresholds inside of a single transaction
Lending Protocol Safety
Guarantee lending positions maintain the required collateralization ratios
Oracle Monitoring
Verify oracle prices stay within specified ranges to detect price manipulation
Balance Invariants
Ensure that the sum of all positions match the total balance of a protocol
Compliance Rules
Enforce KYC/AML requirements by validating that transaction participants meet regulatory criteria
Who It’s For
Protocol Teams
Deploy and manage assertions to protect your contracts
Networks & Sequencers
Integrate enforcement into block building
How It Works
Defining Security Rules
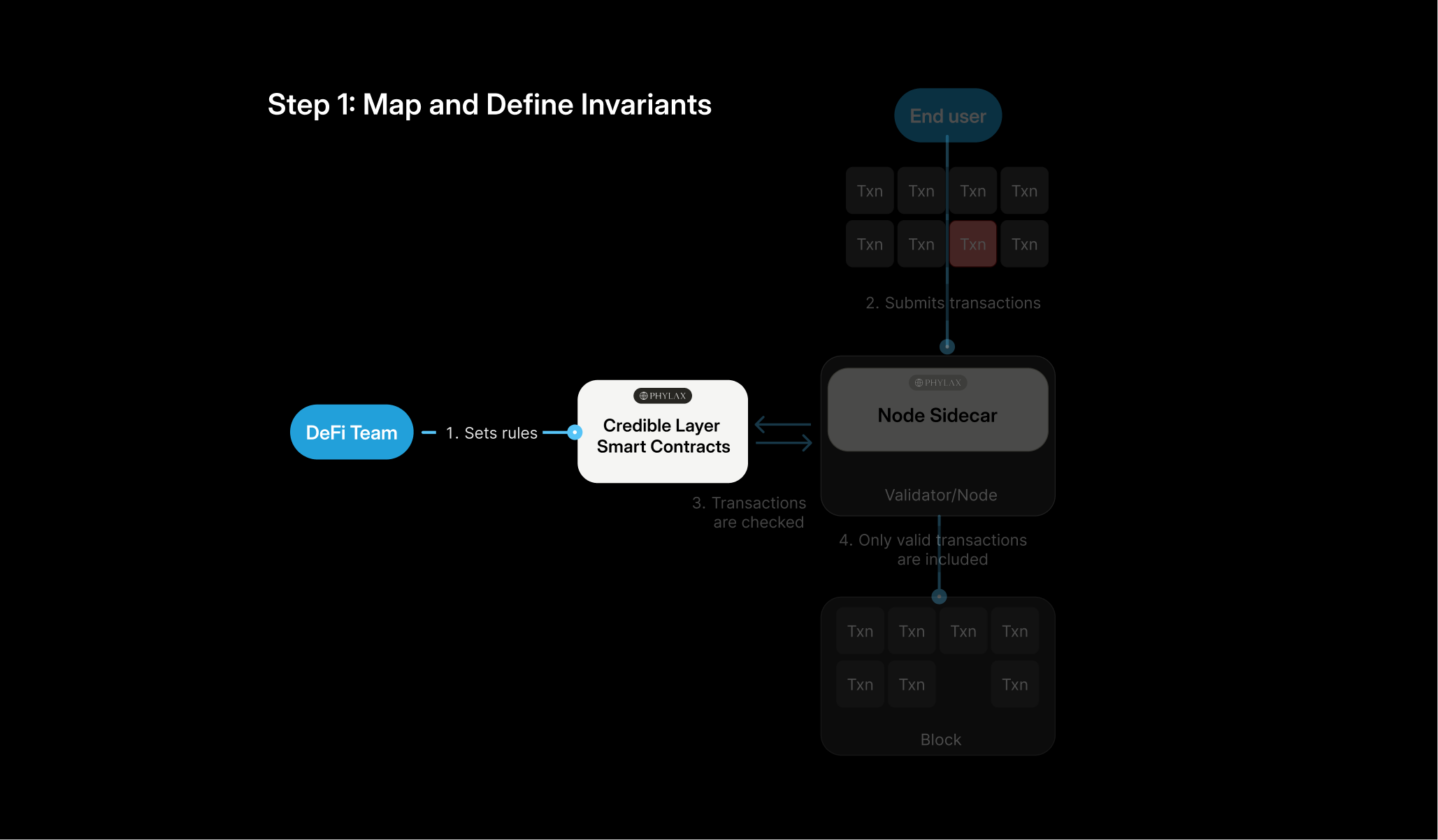
- Timelocks and Access Control: Add time-based restrictions or multi-factor authentication requirements for sensitive functions like contract upgrades
- Business Logic Enforcement: Ensure operational rules are followed, such as transaction limits or authorized contract interactions
Real-World Example: Balancer V2
In November 2025, an attacker exploited Balancer V2 stable pools through a complex rounding error attack, causing over $120M in losses. Through 84 crafted swap operations, pool rates changed by 20x in a single transaction. The key insight: While the root cause was complex (involving rounding errors and specific balance configurations), the security rule violation was simple:“Pool rates should not change drastically within a single transaction”A simple assertion checking that pool rates don’t change by more than 3x would have detected and prevented this attack, regardless of the specific exploit mechanism used.
View the assertion code
View the assertion code
Network Enforcement
Once assertions are defined, they need to be deployed to protect your contracts. This involves submitting the assertion to your project, then linking it to your contract address.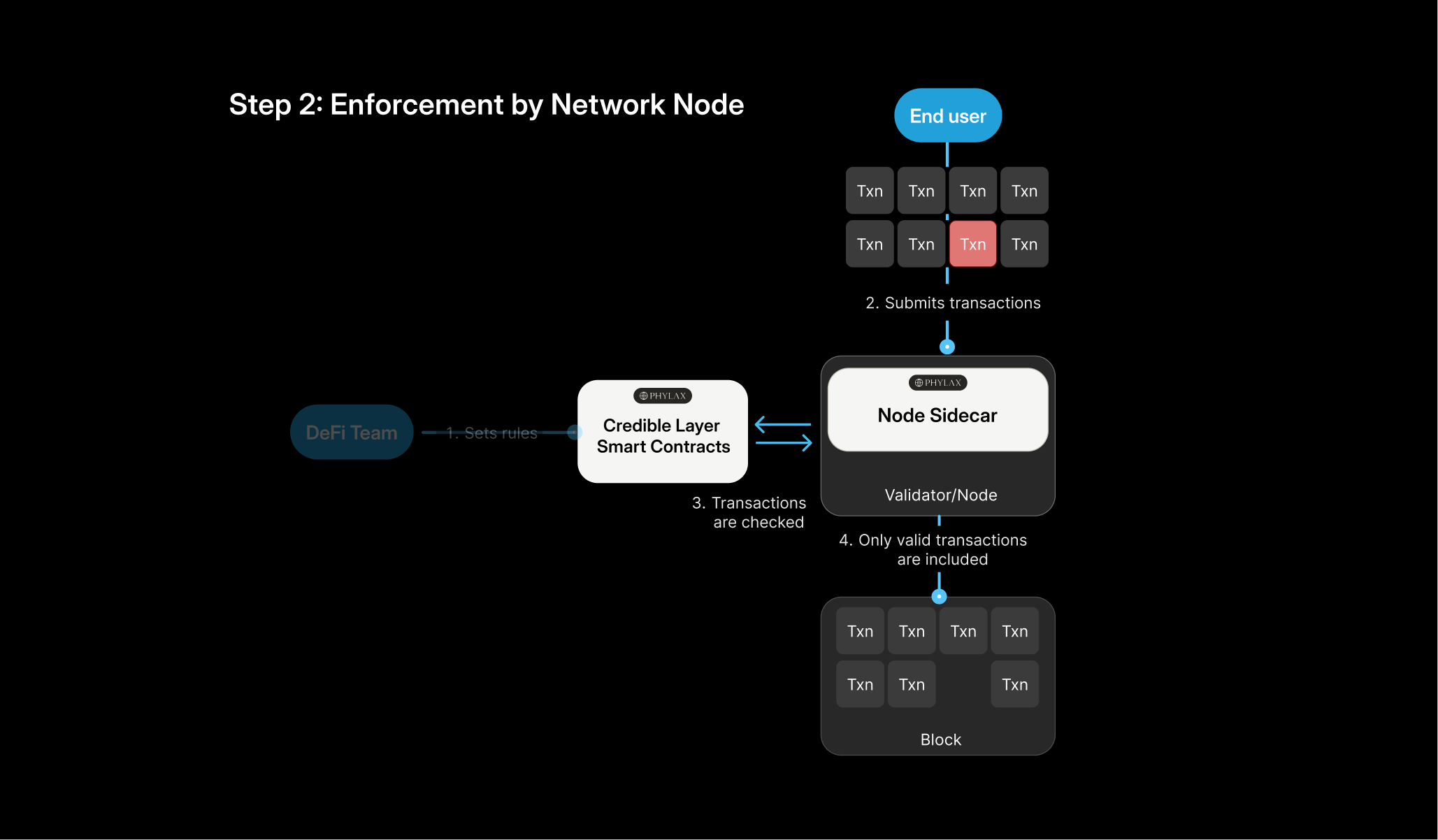
How Enforcement Works
A network node running the Credible Layer sidecar does not care how a transaction violates the protocol’s rule. All that matters is whether the assertion passes or fails. If the assertion fails, the node drops the transaction before it can be included in a block. When a user opens a position on a yield protocol, the transaction may touch multiple contracts: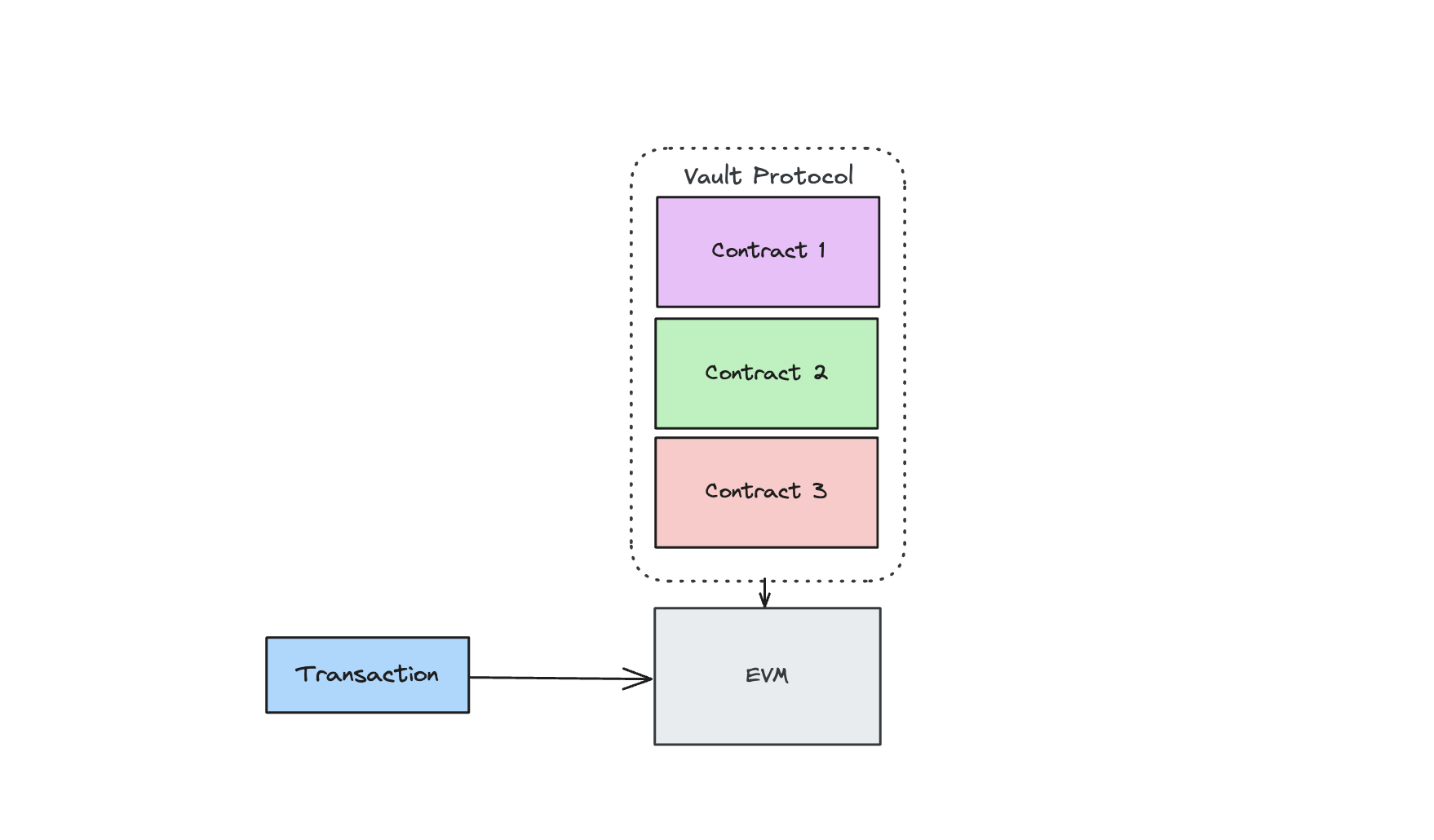
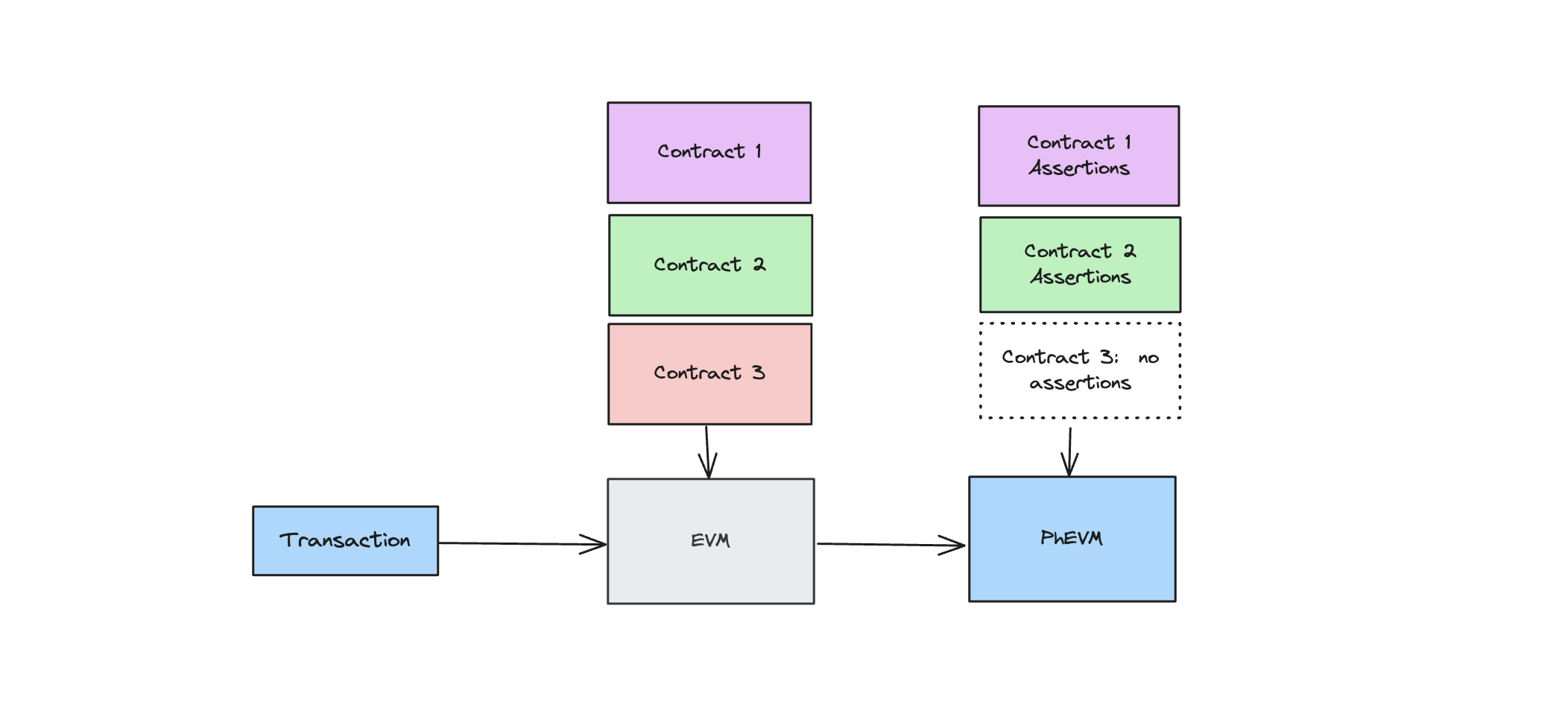
Validation Process
- User submits a transaction to the network
- The network node passes it to the sidecar for validation
- The sidecar simulates the transaction and checks all relevant assertions
- If all assertions pass, the transaction is included in the block
- If any assertion fails, the transaction is dropped
The Credible Layer is designed as neutral middleware that preserves decentralization for both dApps and networks. Learn more about why neutrality matters.

